36. Topic 5, A. Datum Corporation
Overview
A. Datum Corporation is a consulting firm that has a main office in Montreal and branch offices in Seattle and New York.
Azure Environment
A. Datum has an Azure subscription that contains three resource groups named RG1. RG2, and RG3.
The subscription contains the storage accounts shown in the following table.
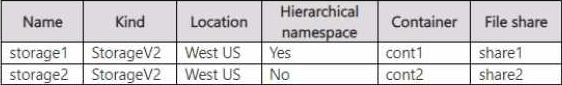
The subscription .contains the virtual machines shown in the following table.
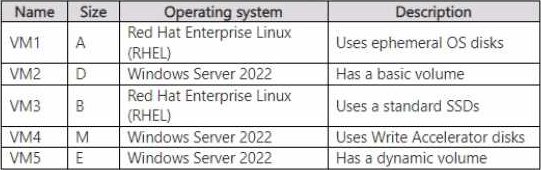
The subscription has an Azure container registry that contains the images shown in the following table.
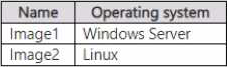
The subscription contains the resources shown in the following table.
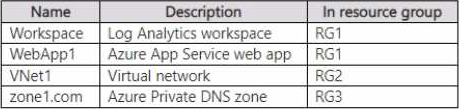
The subscription contains an Azure key vault named Vaultl.
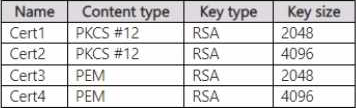
Vault! contains the certificates shown in the following table.
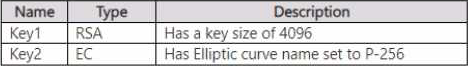
Vaultl contains the keys shown in the following table.
Microsoft Entra Environment
A. Datum has a Microsoft Entra tenant named adatum.com that is linked to the Azure subscription and contains the users shown in the following table.
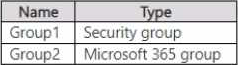
The lenant contains the groups shown in the following table.
The adatum.com tenant has a custom security attribute named Attribute1.
Planned Changes
A. Datum plans to implement the following changes:
• Configure a data collection rule {DCR) named DCR1 to collect only system events that have an event ID of 4648 from VM2 and VM4.
• In storage1, create a new container named cont2 that has the following access policies:
o Three stored access policies named Stored 1, Stored2, and Stored3
o A legal hold for immutable blob storage
• Whenever possible, use directories to organize storage account content.
• Grant User1 the permissions required to link Zone1 to VNet1.
• Assign Attribute1 to supported adatum.com resources.
• In storage2, create an encryption scope named Scope"1.
• Deploy new containers by using Image1 or Image2.
Technical Requirements
A. Datum must meet the following technical requirements:
• UseTLSforWebApp1.
• Follow the principle of least privilege.
• Grant permissions at the required scope only.
• Ensure that Scope1 is used to encrypt storage services.
• Use Azure Backup to back up cont1 and share1 as frequently as possible.
• Whenever possible, use Azure Disk Encryption and a key encryption key (KEK) to encrypt the virtual machines.
You implement the planned changes for Scope1.
You need to ensure that Scope1 meets the technical requirements.
What can you encrypt by using Scope1?
A. containers and blobs in storage2 only
B. containers and blobs in storage1 and storage2
C. containers, blobs, and file shares in storage2 only
D. containers, blobs, and file shares in storage1 and storage2
E. containers, blobs, file shares, queues, and tables in storage2 only

Leave a Reply